Overview
The high-level steps involved in configuring Zoom for SSO with ADFS are:
- Obtain your institutional ADFS SAML metadata (.xml)
- Using your Zoom admin account, access the Zoom SSO configuration page and enable SSO
- Open the “SAML” tab and enter your institutional SAML metadata (obtained from your ADFS SAML metadata file .xml )
- Access your institutional ADFS configuration interface
- Configure the source of SAML relying-party metadata
- Configure the relying-party display name as “Zoom”
- Configure relying-party Assertion Consumer and Logout end-points
- Add claim rules:
- Map and send attributes for E-Mail-Addresses, User-Principal-Name, Given-Name and Surname.
- Configure E-Mail Address as the Name ID outgoing claim type
- Test SSO to Zoom
Detailed Steps
- Find and download/view your ADFS XML metadata at https://[SERVER]/FederationMetadata/2007-06/FederationMetadata.xml.
* [SERVER] is the domain name of your ADFS server (e.g. adfs.university.edu.au) -
From the Zoom Admin page, click on Single Sign-On to vide the SAML tab.
- Enter the following information into the SAML tab options:
- Sign-in page URL: https://[SERVER]/adfs/ls/idpinitiatedsignon.aspx?logintoRP=[VANITY].zoom.us
- Sign-out page URL: https://[SERVER]/adfs/ls/?wa=wsignout1.0
- Identity provider certificate: Note, use the "Signing" certificate.
* Use the first X509 Certificate in the FederationMetadata.xml file (Step 1)
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"> <KeyInfo zmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data> <X509Certificate>
- Issuer: http or https://[SERVER]/adfs/services/trust (entityID in metadata - Step 1)
- Binding: HTTP-POST
- Default user type: Basic or Corp
- Login to you ADFS server, open ADFS 2.0 MMC.
Open the administrative interface of ADFS. - Add a Relying Party Trust
Select Import data about the relying party published online or on a local netowrk
Federation metadata address: https://[VANITY].zoom.us/saml/metadata/sp
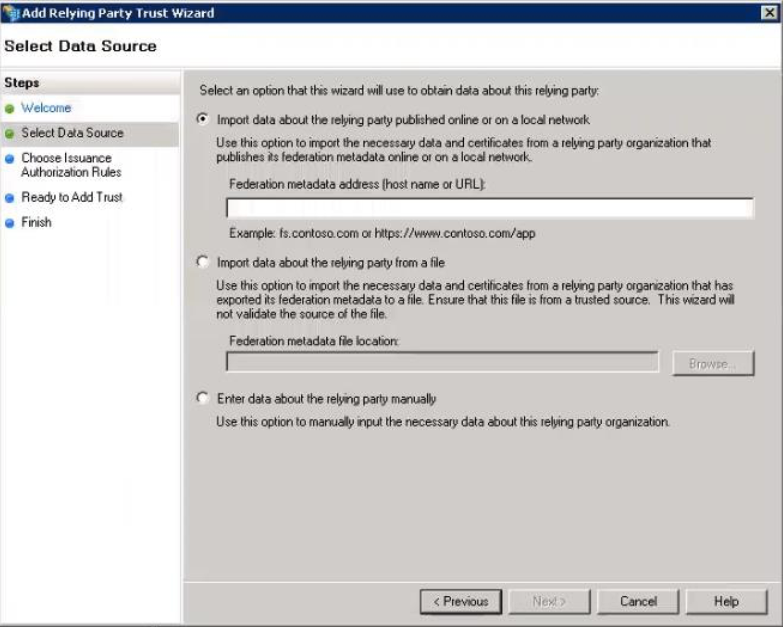
- Add a display name ("Zoom") and finish the Wizard with the default settings.
- Change both Redirect and Post SAML Logout Endpoint URLs to:
(Right click the new Relying Party Trust > Properties > Endpoints tab)
https://[SERVER]/adfs/ls/?wa=wsignout1.0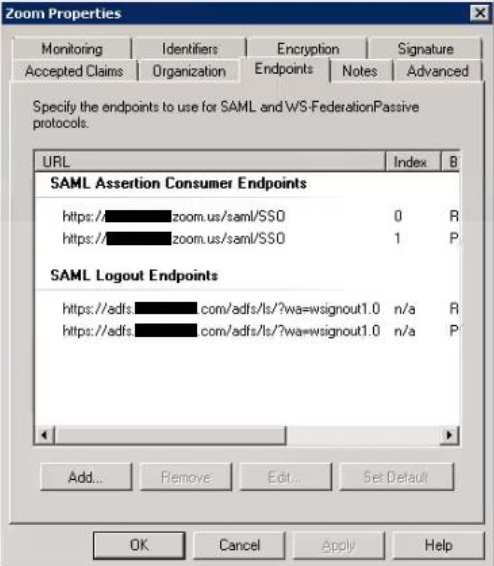
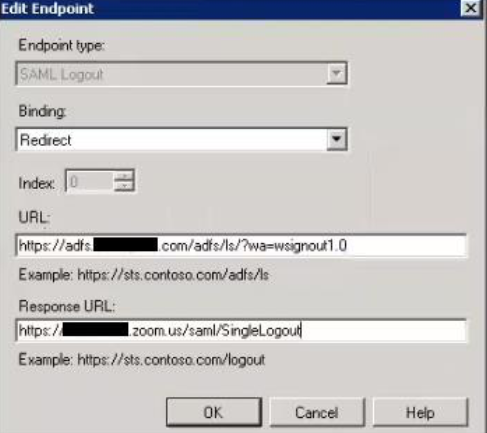
* Note: If you are unable to change the logout andpoints, open the Monitor tab and uncheck "Automatically update relying party" and Apply changes. - Add two claim rules
- First claim rule ...
Type: Send LDAP Attributes as Claims
Name: Zoom-Send to Email
Mappings:
E-Mail-Addresses > E-Mail Address
User-Principal-Name > UPN
Given-Name > urn:oid:2.5.4.42
Surname > urn:oid:2.5.4.4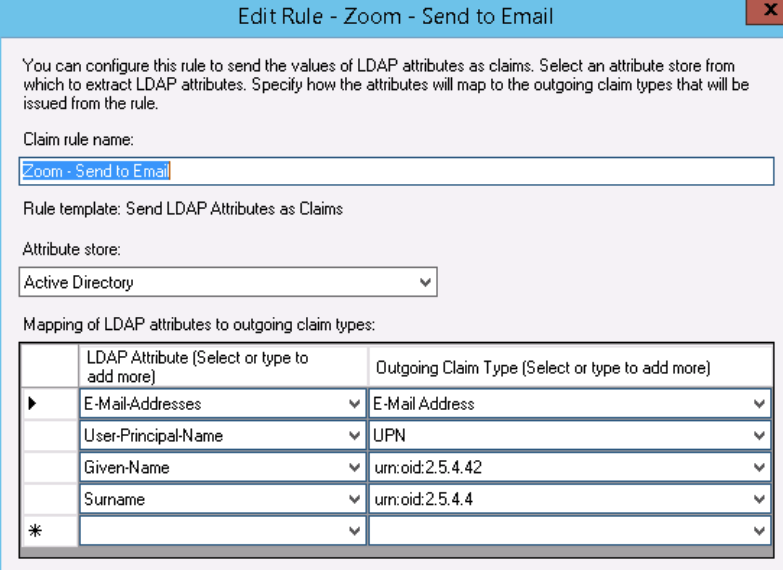
* if User-Principal-Name has email format and is different from E-Mail-Address, you may want to map the User-Principal-Name to E-Mail Address ...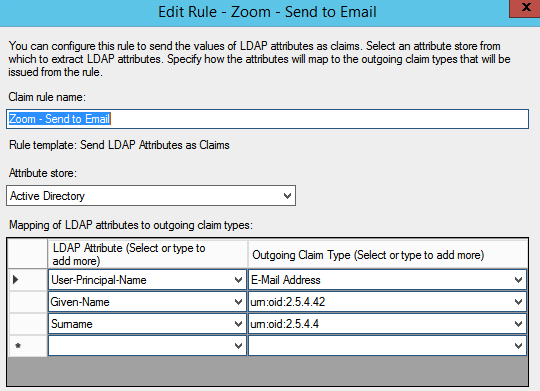
- Second claim rule ...
Type: Transform Incoming Claim
Name: Zoom-Email to Name ID
Incoming claim type: E-Mail Address
Outgoing claim type: Name ID
Outgoing name ID format: Email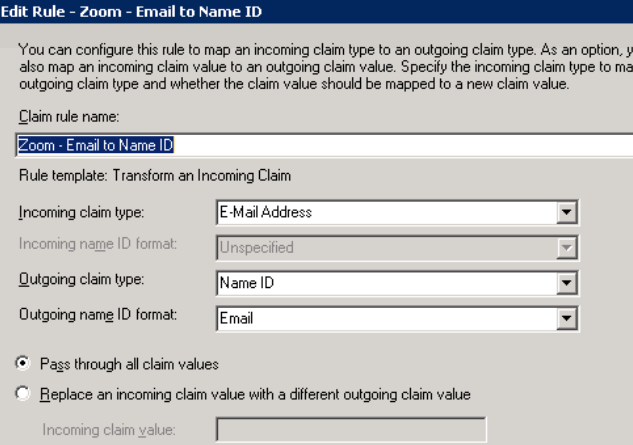
- Test SSO by visiting https://[VANITY].zoom.us/signin.
You should see your institutional login screen.
Troubleshooting Tips
Issue 1: Unable to log in using Google Chrome or Firefox
If you are unable to log in using Chrome or Firefox, and are seeing an 'Audit Failure' event with "Status: 0xc000035b" in the Event Viewer on the ADFS server, you will need to turn off Extended Protection. Chrome and Firefox do not support the Extended Protection of ADFS (IE does).
- Launch IIS Manager
- In the left panel, navigate to Sites > Default Web Site > ADFS > LS
- Double-click Authentication icon
- Right-click Windows Authentication
- Select Advanced Settings
- Turn OFF Extended Protection.